Six out of ten cases of data breaches happen due to unpatched vulnerabilities which only proves that SDLC security should be the #1 priority. Your source code can get into the wrong hands that’s why you need to follow all possible best practices of security in the software development life cycle. Companies like Binariks utilize SSDLC to ensure multi-layer code protection. Keep reading and learn what best practices, processes, tips, and components of secure SDLC ensure high-level code security.
Why implement SSDLC?
Imagine yourself as a project manager: the active development phase is about to start and without a solid plan, it’s hard to keep multifaceted aspects of product engineering on track.
What should you do?
Think in the direction of implementing the security development life cycle. The secure development model will help you control each phase in the development cycle. Especially when it comes to finding a balance between controlling the development pipeline and fulfilling estimated requirements.
And that’s not all, here are five more secure software development lifecycle benefits.
- SSDLC shifts attention to security
Quite often, tech specialists check code security closer to the end of the software development cycle rather than mid-process. Short of time, people tend to turn a blind eye to “smaller” vulnerabilities trying to fix the major flaws.
SSDLC – secure development life cycle integrates security seamlessly into all phases of the software engineering process. In effect, stakeholders become conscious of security.
- SDLC security helps identify and fix vulnerabilities in the early stages
Another benefit of SSDLC is that it predicts the application of security testing protocols. They help engineers identify bugs before they turn into significant issues. This practice saves a lot of time and money.
- SSDLC reduces costs and improves security of development life cycle
Organizations that ignore secure SDLC have copious amounts of vulnerabilities in their software.
Therefore, the expense of fixing faults at an early stage of development is modest in comparison to later phases.
One survey found that fixing a security issue during the requirement or planning stage costs about $10.
And when you identify this bug in the deployment stage, the cost of the bug fix will raise to $2000.
- Secure SDLC gives more time for software testers
Because software testing (including healthcare software testing ) is performed at each level, any problems or issues may be efficiently handled.
As a result, the development team maintains focus and organizes the product release properly. There will be no surprises throughout the manufacturing process using SSDLC.
QA Testing of Primary Care Platform
We conducted QA testing on each stage of SSDLC
How to implement SSDLC?
The journey for creating an SSDLC begins with a secure development model. At Binariks, we follow a 5-step model commonly seen in the industry which breaks down security in software development life cycle into 5 phases:
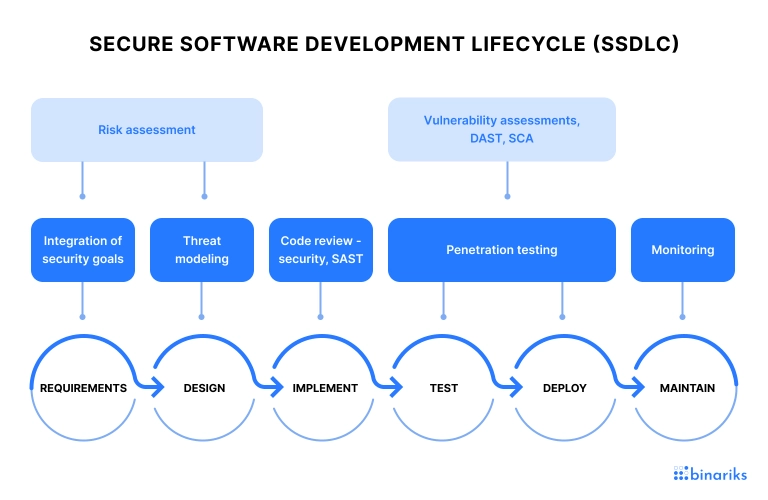
Let’s take a look at how SSDLC can be implemented during every phase of product creation.
- Requirements
The main idea here is to establish the tone and outline the security elements of the impending product or service. It is a crucial chance to improve developer awareness and create a "security first" culture.
Imagine that your team is creating a notification service that will notify users about important events. It’s crucial here to separate tenants and notify those interested in the event. And if the notification contains sensitive data, your team should accommodate a range of security and privacy concerns.
The main goal of this phase is to generate a “threat model” that will be later addressed throughout the entire development lifecycle. As a rule, the model is based on security best practices including ones defined by OWASP.
The threat model is a good foundation for its own requirements workshops. A smart initial step is to plan a requirements session using a generic threat model as a template. Define the concepts and rules to be utilized throughout development and testing at that discussion - what is critical to secure? What are the best security practices? It should also specify any security measures that must be applied during the development lifecycle.
As an alternative, you may plan a modeling and design meeting before you schedule a feature in a sprint log and define who can approve the threat model.
- Design
As a rule, engineering teams create a tech design of the feature. In our example of a notification service, there may be a new microservice, a message queue, a database to hold undelivered messages, and so on. This step requires you to ensure that the security design addresses the threat model created during the requirements phase.
During the design phase, you define which security mechanisms you’ll be using. Here are the key steps to follow:
✅Check the security requirements
✅Find weaknesses and potential design flaws
✅Estimate the severity of various risks through threat modeling techniques. Then, rank them by probability and severity
✅Prioritize the risks for the development team and indicate the non-acceptable risks. Also, think about making a list of items that can be addressed and reduced later
- Development
Integrating security into coding entails developers writing safe code and eliminating security concerns while coding before submitting their final version for additional testing and deployment. Many factors must be addressed in order to do this:
- Education: Training and education would dramatically improve security awareness and mentality. Many team members deal with code updates, and regular training and awareness will aid in detecting anti-patterns and hazards such as data sanitization, communication encryption, and more. OWASP provides numerous excellent training tools and knowing the OWASP Top 10 Security Risks is crucial.
- Code scanning: There are several code analysis scanners available that can detect errors while they are being coded. This includes SAST tools and SCA solutions that target open-source libraries with vulnerabilities. There is a sort of scanner known as an "Infra-as-Code" scanner, or IaC for short, that can identify unsafe setups for numerous infrastructure declaration languages. It is critical to map the set of technologies in use with the scanners accessible in your business.
- Create a repeatable process: Create an operational process that incorporates both of the preceding ideas. For instance, ask developers to use security scanning tools before submitting code, and plan monthly security best practices training refreshers. One method for incorporating security scanning into the process is to employ source-code-management systems (such as GitHub) that use "pull requests," in which developers submit code for a merging, but the update must first pass a series of tests before acceptance. This may necessitate an obligatory SAST scan with explicitly selected persons who have the authority to override a negative result.
- Testing
Having a real agile SDLC means that there is no linear process when you put all processes on halt and do the testing. Most teams today have some kind of CI/CD pipeline in which Continuous Integration takes place and software is regularly tested.
In this mode, a set of tests are carried out at various phases. Some take place during development, some after each code submission, some at night, and others during testing of the live production environment.
It is vital to map out where security tests should be done at the requirement stage. We already discussed testing throughout the coding phase. But, further tests before deployment are conceivable; it all depends on your release plan.
We’d like to highlight two key areas of this phase:
- Based on your release plan, determine which tests you need and where to perform them
- Implement the tests, ideally automatically, so that feedback reaches the developer quickly
- Deployment and maintenance
It's all about establishing a reaction strategy and staying one step ahead of the attacks throughout this time. You must create systems that allow you to be informed when a new external risk is discovered, and keep an eye on emerging security threats, trends, and remedies.
- Keep up with security developments and technology. Security experts and cybercriminals are engaged in an ongoing arms race. The security community releases new threat models, and security technology and methodologies are always evolving.
- Examine external risks. Techniques such as penetration testing are vital here. They will capture threats that may have gotten past all prior security measures. Do these on a regular basis to increase your chances of finding them.
- Handle alerts. Some tools will give you threat intelligence based on recent disclosures. For example, the log4shell vulnerability had existed in production for some time, but once it was properly acknowledged, SCA tools warned their users and security teams, allowing them to rapidly block and remove the susceptible components. You must also anticipate that there are "0-day" vulnerabilities in your apps that might be found at any time.
Improve quality of your digital product with us
Our SSDLC best practices?
Our cross-functional teams follow the SSDLC best practices in every project we deliver. To make sure that SDLC is secure, we follow a set of secure software development lifecycle best practices including the ones mentioned below.

Besides following all necessary rituals and practices throughout the product development process, we also see great value in conducting the following tests and validations.
- We run Dynamic Analysis Security Test (DAST)
DAST is usually applied to the Test/Stage environment. Its main goal is to define and establish DAST processes and apply those to CI/CD pipeline. Remember that DAST should run for major backend tech stack: NET, Java, Python, Ruby, PHP, NodeJs, and C++.
- We set up Static Analysis Security Test (SAST)
We apply SAST to the development environment. Our team runs this test to define and establish SAST processes and apply those to CI/CD pipeline. If you want ot run it, too, mind that SAST should run for major backend tech stack: NET, Java, Python, Ruby, PHP, NodeJs, C++.
- We make version control gated check-in validations
We use this approach to define and establish processes that should be initiated before code is committed into the branch. If you want to apply it as well, make sure that the gated check-in rules are compatible with the top backend programming languages: NET, Java, PHP, Python, NodeJS, Ruby, С++.
SSDLC challenges
There are various problems that might jeopardize the security of SDLC deployment. The inability to effectively account for and meet customer and stakeholder demands in the process is perhaps the most critical issue. As a result, system needs are misunderstood, and the ultimate result is unavoidably disappointing.
Moreover, the SDLC's complexity frequently leads a project to derail or teams to lose sight of specifications and needs. A project might easily fall short if all specifications and design plans are not strictly followed.
Final thoughts
Conventional methods of testing for vulnerabilities in production are no longer enough for protecting your apps. As the software business has grown, so have the sorts of assaults. To deploy and maintain a secure application, every stage of the application development process must be secured through SSDLC and cyber security best practices. This includes asking questions about security behaviors during the requirement gathering stage, modifying team culture and practices to account for a security-oriented mindset, incorporating automated verification into your deployment process, and a variety of other practices that contribute to a secure SDLC process.
Instead of needing to backtrack from the maintenance phase, SSDLC allows you to move security risks to the left, addressing the source of security concerns at the requirements phase. You can be confident that your application will be significantly more secure as a consequence of concentrating on security at every step of development.
FAQ
Share

