Hybrid cloud architectures – combining private infrastructure with public cloud services – have become the dominant deployment model for enterprises managing AI workloads, sensitive data processing, and regulatory compliance requirements.
Gartner forecasts that by 2027, 90% of organizations will have adopted hybrid cloud strategies, yet security remains the primary barrier to cloud adoption, with organizations struggling to maintain consistent controls across fragmented infrastructure.
Companies running AI-driven operations, such as financial reporting systems or customer analytics platforms, face amplified security complexity. These workloads require scalable compute resources (public cloud) while handling regulated data (private infrastructure).
The challenge isn't choosing between cloud models – it's securing the integrations, data flows, and access controls that span both environments. When hybrid cloud security fails, consequences include data breaches, compliance violations, and operational disruptions that directly impact business continuity.
AI workloads intensify these risks by processing large datasets across distributed systems, creating expanded attack surfaces and visibility gaps that traditional security tools weren't designed to handle.
A robust hybrid cloud security architecture addresses these challenges through unified identity management, end-to-end encryption, zero-trust principles, and automated monitoring – enabling organizations to leverage cloud scalability without compromising data protection.
In this article, we demonstrate the pathway for companies to achieve hybrid cloud security that supports AI-powered operations, regulatory compliance, and business resilience.
What is hybrid cloud security?
Hybrid cloud security is a set of policies and practices used during the adoption of hybrid cloud infrastructure when an organisation uses on-premises infrastructure and public and private clouds simultaneously. The primary goal is to ensure the confidentiality, integrity, and availability of data throughout this distributed architecture.
Naturally, hybrid cloud data protection is different from both private and public clouds. Compared to public cloud security, it has to account for multiple environments and providers. Maintaining unified policies that span both cloud and on-premises systems is complicated because it makes risk management and compliance more challenging.
Compared to private cloud security, a hybrid cloud security model includes external platforms with broader attack surfaces and cross-environment data flows. This makes secure integration a central challenge.
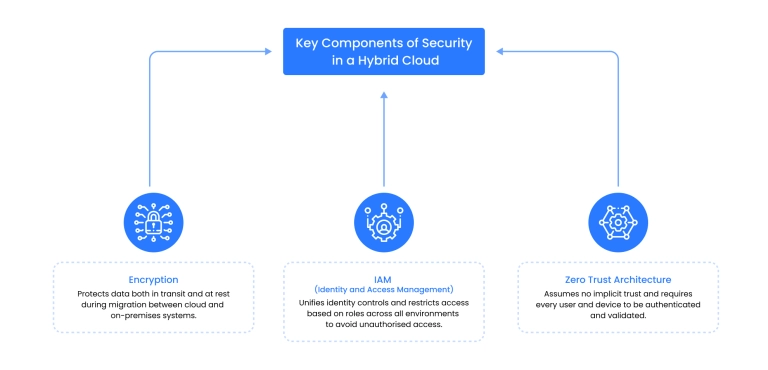
Hybrid cloud security architecture overview
Hybrid cloud security has a recognizable structure. The following are all components of a hybrid cloud security architecture. Note that security controls between them need to be integrated.
Centralized identity and access management (IAM)
This is a system that controls user access and permissions across cloud and on-premise environments through centralized authentication and authorization.
- Encryption and key management
These are techniques and systems used to protect data by converting it into unreadable formats and securely managing the encryption keys throughout their lifecycle.
- Unified security policies and compliance controls
A framework that applies consistent security policies across all environments in a hybrid cloud infrastructure.
- Zero trust network access (ZTNA)
A security model that requires strict identity verification every time for every person and device trying to access resources, regardless of who they are and their location.
- Security monitoring and incident response
A set of tools and processes used to detect, analyze, and respond to security threats using centralized logging, real-time monitoring, and automated workflows.
- Microsegmentation and firewalls
Security strategies that divide networks into isolated segments and use rules or firewalls to control traffic between them.
- Integration layer for security controls
A coordination layer using APIs and control planes to unify and automate various security tools (e.g., IAM, encryption, compliance monitoring) across hybrid environments.
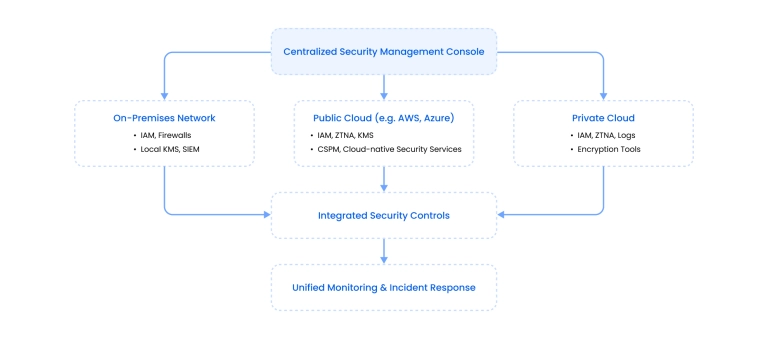
Key challenges and risks in hybrid cloud security
The main benefit of hybrid cloud environments is that they combine the security control of on-premises infrastructure with the scalability and flexibility of public cloud services.
However, they also introduce a range of unique hybrid cloud security challenges that don't exist in single-environment deployments.
1. Expanded attack surface
because there is simply a wider range of components that could be compromised. On-premises, private cloud, and public cloud components all have distinct vulnerabilities that attackers can exploit – and each integration point creates additional entry vectors.
2. Inconsistent security policies
Different environments, including legacy and cloud-based applications, operate under different access rules and encryption methods. This mix of security policies creates weak spots that attackers can exploit. Companies need centralized policy orchestration to mitigate these risks.
3. Limited visibility and monitoring gaps
Security teams often can't see what's happening across all systems in real time when security telemetry is fragmented. Scattered logs may allow security threats to go undetected. As a result, proper incident response is delayed or never triggered. A unified monitoring system provides end-to-end visibility and correlates events across all infrastructure layers.
4. Compliance and regulatory complexity
Requirements such as GDPR, HIPAA, SOC 2, or PCI-DSS become more difficult to satisfy when data moves across platforms with varying controls. If public cloud controls meet strict standards but private infrastructure doesn't, the entire system fails compliance audits. Automated compliance checks and unified audit trails are essential for maintaining continuous compliance posture.
5. Tooling fragmentation
Organizations often rely on a mix of separate tools for cloud and on‑prem systems. Fragmentation becomes even worse in architectures that sit between cloud native and cloud-based environments. To implement effective hybrid cloud security architecture, these tools should be either consolidated or integrated through a unified security operations platform.
Partnering with hybrid cloud security experts like Binariks helps organizations reduce these risks not through a single tool, which is insufficient for such mitigation, but through building a comprehensive security infrastructure that includes:
- Unified security management across on-prem and public infrastructure
- Automation of security controls and audits
- Centralized monitoring and real-time incident response
- Integration of DevSecOps practices into continuous delivery pipelines
Hybrid cloud security best practices
Companies must adopt a strategic, multi-layered approach to hybrid cloud security that addresses all hybrid cloud security risks systematically.
Here is how hybrid cloud security best practices look from our perspective, having worked with dozens of companies seeking a hybrid cloud security solution.
Implement a zero-trust security model
Start by doing this. Zero Trust means that access is granted based on identity, not network perimeter location, and every user, device, or application must be verified each time they access resources. This is the most effective way to contain threats by not automatically trusting any user or device.
Key tactics for a zero-trust security model:
- Identity-based access control, not network-based trust
- Micro-segmentation of workloads and environments to limit lateral movement
- Multi-factor authentication and conditional access policies
- Real-time policy enforcement and validation of each session
Centralize identity and access management (IAM)
Identity and Access Management (IAM) is a practice that ensures the right individuals (or systems) have the right access to the right resources at the right time for the right reasons. A centralized IAM platform is the best practice for consistent enforcement of security policies across the entire system.
IAM serves as the foundational layer for both Zero Trust architecture and future audits.
Its key focus areas include:
- Single sign-on (SSO) and role-based access controls (RBAC)
- Directory synchronization across on-prem and cloud (e.g., Azure AD, Okta)
- Unified policy definitions for all environments
- Logging of all authentication and authorization events
- Multi-factor authentication (MFA)
- Least-privilege access, granting users only the minimum permissions required for their role
- Unified authentication flows across hybrid infrastructure
Encrypt data at every stage
Encryption renders data unreadable to unauthorized users even if they access it. Encryption should protect sensitive data across three states:
- In transit: TLS 1.3 or higher for services, APIs, and remote connections
- At rest: AES-256 encryption across storage systems
- In use: Confidential computing or data masking for active processing workloads
Additionally, use Key Management Services (KMS) and Hardware Security Modules (HSMs) to centralize encryption key management and enforce key rotation policies.
Tokenize sensitive data strategically
Tokenization protects sensitive fields (e.g., card numbers, patient IDs) by replacing them with non-sensitive substitutes, both internally and externally.
Here are the tokenization best practices:
- Use format-preserving tokenization to maintain data usability
- Design a vaulted token architecture for secure mapping and storage
- Know when to tokenize vs encrypt: tokenize for long-term storage, encrypt for transmission
- Choose irreversible tokens for compliance, or reversible with strict key control
Use unified monitoring and logging
Centralized visibility is the key to detecting breaches and misconfigurations early across the entire hybrid cloud security architecture.
Effective monitoring and logging includes:
- Cloud-native tools (AWS CloudTrail, Azure Monitor) integrated with SIEM platforms (Splunk, Sentinel, Chronicle)
- Real-time alerts and dashboards for hybrid infrastructure
- Unified logging formats – with correlation IDs across environments
- Compliance event tagging (GDPR, HIPAA access logs, etc.)
Automate security with DevSecOps
Security must be embedded throughout the entire cloud development and deployment pipelines. DevSecOps – Development, Security, and Operations – represents a modern approach that integrates these three disciplines into continuous delivery workflows.
Here are the key DevSecOps practices:
- Automated code scans and container vulnerability checks in pre-commit hooks and CI pipelines
- Infrastructure as Code (IaC) security policies (use tools like Terraform, Sentinel, and Open Policy Agent)
- Continuous compliance checks in CI/CD pipelines
- Automated remediation of misconfigurations through policy-as-code enforcement
This reduces the attack surface and enforces consistency across hybrid environments.
Conduct regular audits and maintain compliance
Hybrid cloud environments require tailored approaches to regulatory compliance. Audits identify potential vulnerabilities before attackers can exploit them. Here's what effective compliance programs include:
- Control mapping across cloud and on-prem (e.g., ISO 27001, NIST SP 800-53)
- GDPR data residency requirements and HIPAA hybrid guidance compliance
- PCI-DSS tokenization and encryption rules for payment workflows
- Regular internal audits and third-party assessments regularly
- Quarterly access permission reviews
- Compliance-as-code frameworks and automated control mapping tools to eliminate manual audit preparation
Hybrid cloud compliance and regulations
Hybrid cloud compliance operates on the principles of compliance automation and policy orchestration. Compliance automation refers to the use of software tools to automate the management and monitoring of compliance activities across an organization. Policy orchestration is the process of centrally managing the lifecycle of internal security and compliance policies across hybrid infrastructure.
Let's look how to follow each standard for hybrid cloud compliance:
HIPAA (Health Insurance Portability and Accountability Act)
HIPAA is A U.S. federal law that mandates safeguards to protect Protected Health Information (PHI) held by healthcare providers, healthcare insurers, and their vendors (Business Associates).
Scope: Applies to hospitals, clinics, insurers, EHR vendors, and cloud services storing or processing health data.
Key requirements:
- Role-based access controls (RBAC)
- Comprehensive audit logging of all PHI access
- Data encryption (at rest and in transit)
- Regular security risk assessments
PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS is a security standard developed by major credit card companies (Visa, Mastercard, etc.) to protect cardholder data and reduce credit card fraud.
Scope: Applies to any entity that stores, processes, or transmits credit card data (merchants, payment processors, SaaS platforms, etc.).
Key requirements:
- Network segmentation
- End-to-end encryption or tokenization
- Strong authentication and password controls
- Continuous monitoring and logging
GDPR (General Data Protection Regulation)
GDPR is a European Union regulation that governs how organizations handle the personal data of EU citizens.
Scope: Applies to any company (inside or outside the EU) offering goods or services to EU citizens or processing their data.
Key requirements:
- Lawful basis for data collection
- Consent management systems
- Data minimization and portability
- Right to access, rectification, and erasure (“right to be forgotten”)
SOC 2 (System and Organization Controls) / ISO/IEC 27001
SOC 2 is a U.S.-based audit framework for evaluating internal controls for service organizations based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
ISO/IEC 27001 is an international standard for managing information security via a formalized Information Security Management System (ISMS).
Scope: Apply to SaaS providers, cloud service providers, and vendors handling sensitive or regulated data. ISO/IEC 27001 also applies to companies outside tech (e.g., manufacturing, finance, logistics).
Key requirements:
- Formal security policies and procedures
- Risk assessment and mitigation plans
- Third-party vendor management
- Access control and incident response protocols
FedRAMP / NIST (U.S. Federal Risk and Authorization Management Program / National Institute of Standards and Technology)
FedRAMP is a U.S. government program that standardizes security assessment, authorization, and continuous monitoring for cloud products used by federal agencies.
NIST SP 800-53 is a catalog of security and privacy controls for federal information systems and contractors handling Controlled Unclassified Information (CUI).
Scope: FedRAMP applies to cloud service providers (CSPs) wanting to sell to the U.S. federal government. NIST SP 800-53 applies to federal agencies and contractors managing CUI.
Key requirements:
- Control families across access control, incident response, system integrity, etc.
- Formal System Security Plans (SSPs)
- Continuous monitoring programs and automated security assessment tools
Binariks' expertise in hybrid cloud security
Binariks is an expert in helping companies build hybrid cloud infrastructures in high-stakes industries such as banking, healthcare, and insurance. Our approach combines cloud architecture, data protection, DevSecOps, and compliance automation.
Our goal for hybrid cloud implementation is to build secure operating environments that meet regulatory expectations and business needs simultaneously.
Here are the hybrid cloud security solutions we offer to our clients:
- Hybrid Cloud Architecture Design
- Google Cloud consulting
- Data Security & Tokenization based on Protegrity
- DevSecOps Integration using tools like Terraform, Jenkins, Vault, and GitOps. This includes infrastructure-as-code, secrets management, zero-trust access, and automated enforcement of compliance policies.
- Compliance Automation (PCI-DSS, GDPR, HIPAA, and regional data laws)
- Legacy System Modernization with resilient frameworks like Apache Spark and real-time ingestion via Kafka.
- Unified Monitoring and Incident Response using Splunk and CloudWatch for faster incident resolution across cloud and on-prem layers.
One of our recent hybrid cloud security projects was delivered to a leading banking group in the Middle East, which operates across multiple countries and generates over $400 million in revenue. It was a hybrid cloud data platform for multi-country banking .
The bank faced the urgent need to modernize its reporting and analytics stack, but a couple of challenges blocked full cloud adoption:
- Strict data residency laws required that PII, cardholder data, and financial records be all kept on-premises.
- PCI-DSS required the bank to secure and track all payment data.
- Legacy systems (Oracle/MS SQL) were too slow and expensive to maintain.
- Data quality suffered due to mismatched definitions and manual Qlik-based ETL.
- IT teams were overloaded, with no self-service and long delays for reports.
Binariks designed and delivered a secure, enterprise-wide hybrid cloud data platform with:
- A dual-layer architecture:
- On-prem with sensitive data tokenized in real time using Protegrity.
- Cloud (AWS) with de-identified and analytic workloads moved to AWS S3, EMR (Spark), RDS, and DynamoDB.
- A unified access layer. Business users accessed data through a single logical interface with centralized governance and role-based access control (RBAC).
- Real-time ingestion and analytics:
- Kafka was used for high-throughput streaming of transactional data.
- Spark pipelines replaced Qlik ETL because they provided better real-time insights.
- With Tableau and Jupyter, teams could explore and analyze data independently without the IT department's help.
- Compliance and audit readiness:
- The system automatically tracked data flow, tokenization activity, and user access.
- This helped the bank meet PCI-DSS requirements and pass internal audits.
Here are the results achieved with our hybrid cloud security architecture:
- Data latency reduced from 24 hours to near real-time
- Reporting time cut by 80%, making way for same-day campaign and fraud decisions
- Regulatory audit preparation time lowered by 25%
- Legacy system licensing costs reduced by 40%
- Made real-time fraud detection, credit scoring, and 360° customer views possible.
- Scaled to support 1000+ users per day and millions of daily transactions
Overall, this solution transformed the bank’s data infrastructure into a secure, compliant, and innovation-ready hybrid platform, which is now considered a model for digital modernization in the Middle East region. For an extra case illustrating our work, see how we helped another client in scaling enterprise file collaboration .
Conclusion: The future of hybrid cloud security
Hybrid cloud application security protects your organization using methods such as Zero-Trust Network Access (ZTNA), Centralized Identity and Access Management (IAM), end-to-end encryption, microsegmentation, and automated DevSecOps practices across both cloud and on-premises environments.
Hybrid cloud helps you combine the scalability and flexibility of the cloud with the security of the on-premises environment, so it is a must for business operations in 2026 and beyond.
However, it also creates an expanded surface for potential vulnerabilities, so it is important to follow best practices when establishing hybrid cloud data protection.
Binariks can help design and implement a hybrid cloud security solution tailored to your data and industry's highest standards.
Share

