Enterprise security leaders face a recurring challenge: their systems pass compliance audits yet still suffer breaches. The disconnect often stems from treating two complementary security practices – penetration testing and threat modeling – as interchangeable tools.
Some teams expect a pentest to uncover every possible risk, while others rely solely on threat modeling and assume it will cover all uncertainties. This leads to familiar pain points: hidden vulnerabilities, delayed releases, inefficient use of security budgets, and systems that appear secure only on paper.
In practice, the two approaches operate at different stages of the product lifecycle and work best together. Threat modeling functions as architectural risk analysis, identifying risks early in the design phase, while penetration testing validates how well your controls stand up to real attacks.
Organizations that understand this distinction build a cohesive, reliable security process rather than isolated one-off checks.
In this article, you’ll learn:
- Why threat modeling and pentesting solve different security problems
- When each approach delivers the highest value
- How they complement each other in a continuous security workflow
- Which tools and frameworks help teams get started quickly
Ready to dive in? Let’s break down both practices and see how they work together.
What is threat modeling?
Threat modeling is a category of proactive security methodologies that analyzes system architecture for potential attack vectors before development begins, when security decisions are flexible to adjust.
Unlike reactive security testing, threat modeling operates as a design discipline – similar to how architects assess structural integrity before construction.
This distinction is essential when comparing penetration testing vs threat modeling. By catching issues at the design stage, organizations optimize their security budgets – investing in prevention rather than expensive remediation after the system is already deployed.
Key methodologies
One of the most widely used methodologies is STRIDE, which breaks threats into six clear categories:
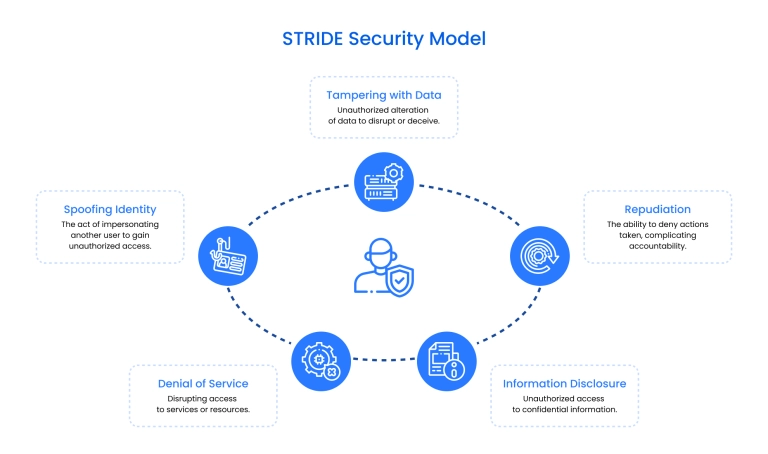
For complex or distributed environments, many teams use PASTA (Process for Attack Simulation and Threat Analysis).

PASTA follows a seven-stage, risk-centric workflow that maps business objectives, attacker capabilities, and technical vulnerabilities. It’s particularly useful for systems with multiple integration points, diverse user groups, or high-value data flows that require deeper attack-path modeling.
These structured methodologies also strengthen threat modeling in penetration testing, helping teams define scope, highlight likely attack vectors, and focus pentesting efforts on areas where real-world impact would be the highest.
What is penetration testing?
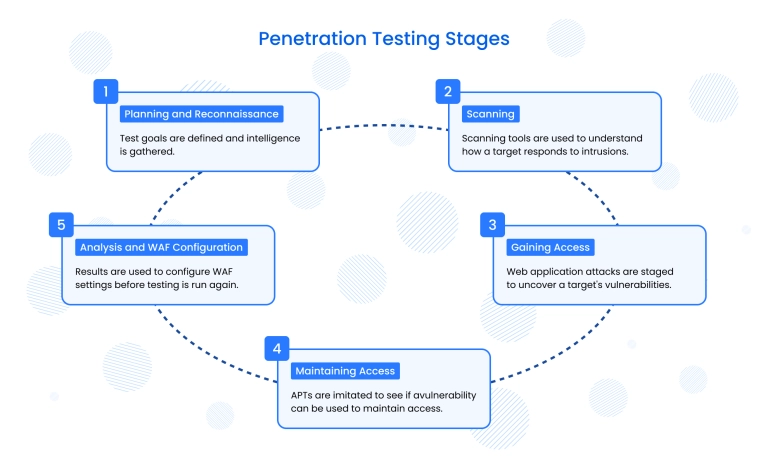
Penetration testing is a controlled simulation of a cyberattack performed to identify security weaknesses in a system that is already running in production.
A penetration test, or ‘pen test,’ is a security test that launches a mock cyberattack to find vulnerabilities in a computer system. This makes it fundamentally different from penetration testing or threat modeling, where the latter predicts risks during design instead of validating defenses after deployment.
Pentesters (ethical hackers) use offensive techniques to uncover vulnerabilities that typical reviews overlook. Ethical hacking is a broader discipline, but penetration testing is its focused method for probing apps, networks, APIs, cloud assets, and integrated systems under realistic attack conditions.
Security teams rely on several established frameworks to structure the process:
- OWASP Testing Guide, which outlines web application security testing techniques.
- PTES (Penetration Testing Execution Standard), covering intelligence gathering, threat modeling, exploitation, and reporting.
- Custom methodologies adapted to cloud-native architectures and DevOps-based delivery models, especially in organizations that need DevOps to streamline engineering workflows.
Pentesting is a reactive practice: it verifies whether implemented controls actually work, where attackers could break through, and how deeply they could move inside the system. The lifecycle commonly includes planning, reconnaissance, scanning, gaining access, maintaining access, and post-test analysis – all focused on real adversarial behavior.
This is why threat modeling in a penetration testing workflow matters. Early threat analysis highlights high-value assets and probable attack paths, allowing pentesters to target the areas that matter most. For CTOs operating under budget constraints, this ensures security spending goes exactly where it delivers measurable impact.
Threat modeling vs. penetration testing
Organizations often treat these two practices as interchangeable. However, this misunderstanding creates predictable security gaps: teams either over-invest in late-stage testing while ignoring design flaws, or they produce comprehensive threat models that never face real-world validation.
The fundamental distinction is that threat modeling and penetration testing solve different problems at different stages of the security lifecycle.
- Threat modeling helps teams anticipate risks early, while pentesting validates how resilient the system is once it’s live. It answers the question: "What could an attacker target, and how do we design defenses into the system architecture?"
- Penetration testing operates as a validation control – an offensive simulation that confirms whether implemented security controls withstand real adversarial techniques. It answers: "Can our deployed defenses actually stop the attacks we designed them to prevent?"
Therefore, for CTOs trying to balance limited budgets, compliance pressure, and real-world risk, the right question isn’t which one to choose, it’s how to use both effectively.
The comparison table below breaks down nine evaluation criteria that clarify when each practice delivers maximum value and how they differ in execution:
| Criteria | Threat Modeling | Penetration Testing |
| Core objective | Identify potential threats, vulnerabilities, and weak design assumptions before development. | Discover real, exploitable vulnerabilities by simulating adversarial attacks. |
| Stage of implementation | Early design and architecture phases, before code or infrastructure is deployed. | After deployment or before major releases; also used on running production systems. |
| Primary focus | Predictive analysis: how the system could be attacked and what to fix by design. | Validation: how attackers would exploit weaknesses in real-world scenarios. |
| Approach | Uses structured frameworks (STRIDE, PASTA) to map attack paths and define mitigations. | Uses offensive techniques guided by OWASP, PTES, and custom testing workflows. |
| Type of practice | Proactive – prevents defects and reduces long-term security costs. | Reactive – confirms control effectiveness and uncovers missed vulnerabilities. |
| Outcome | Prioritized list of risks with recommended design and architectural mitigations. | List of successfully exploited vulnerabilities with remediation guidance. |
| Team involvement | Architecture, engineering, product teams. | Security engineers, ethical hackers, DevOps/infra teams. |
| Budget impact | Saves cost by preventing issues before they reach production. | Requires defined scope; cost depends on system size and testing depth. |
| Ideal use case | Planning new systems, major redesigns, threat-driven architecture decisions. | Validating existing controls, preparing for audits, hardening production systems. |
When combined, both approaches create a continuous, reliable security workflow that avoids the “compliance checkbox” mindset and builds long-term resilience.
Bringing threat modeling and pentesting together
Threat modeling and pentesting, often discussed as separate options, work best as a unified, repeatable process. An effective approach to threat modeling and penetration testing aligns early design-stage analysis with real-world attack simulations, giving CTOs a clearer view of where to invest, what to fix, and how resilient their systems actually are.
This integration mirrors how teams structure broader engineering disciplines, such as quality assurance services , where continuous feedback loops replace one-off checks.
This integrated security workflow operates as a five-stage cycle, with each phase producing inputs that inform the next:
- Start with threat modeling (preventive analysis phase)
Teams map assets, attack paths, and design assumptions using STRIDE or PASTA. This creates a focused list of high-risk areas that need deeper inspection. The primary output is a prioritized threat register that identifies which system components, data flows, and trust boundaries present the highest attack probability and business impact.
- Translate insights into pentest scope (targeting phase)
Instead of broad or generic testing, pentesters target the pathways with the highest potential impact. This ensures the budget is spent where it moves the needle.
Threat model findings directly shape the rules of engagement, attack scenarios, and success criteria for offensive testing – transforming theoretical risks into testable hypotheses.
- Run pentesting based on realistic attack behavior (validation phase)
Ethical hackers validate which assumptions hold and which break under pressure, revealing actual exploitable vulnerabilities. This empirical testing confirms whether architectural security controls function as designed or whether implementation gaps create exploitable weaknesses that threat modeling couldn't predict.
- Feed results back into design and engineering (learning phase)
Findings refine future architecture decisions, improve early risk models, and shape updated threat scenarios.
Pentest discoveries update the organization's threat intelligence library, creating more accurate assumptions for subsequent threat modeling exercises and establishing patterns that prevent similar vulnerabilities in future projects.
- Repeat as systems evolve (continuous security phase)
Every new feature, integration, or architectural change reopens the attack surface. Continuous security means repeating both practices over time, not treating them as annual checkboxes.
This cyclical approach treats security as a product lifecycle discipline rather than a compliance event – similar to how continuous integration validates code quality with every commit rather than once per release.
When threat modeling guides the intent of testing, and pentesting validates the real-world impact of design decisions, organizations build a security program that is adaptive, cost-efficient, and grounded in actual risk, not assumptions or compliance pressure.
This bidirectional relationship, where design analysis informs testing priorities, and testing results improve design practices, creates a self-reinforcing security maturity cycle that strengthens with each iteration.
Tools and techniques to get started
Building a balanced security workflow requires tools that support both architectural analysis and real-world attack validation. Companies adopting penetration testing and threat modeling typically blend open-source and commercial solutions to stay efficient while still maintaining depth.
Below is a list of established tools, organized by their primary function within the security lifecycle – each with clear use cases that help teams match capabilities to their operational maturity and architectural complexity.
Threat modeling tools
1. Microsoft Threat Modeling Tool
A standards-based platform built around data-flow diagrams and STRIDE. Ideal for engineering teams that want to integrate modeling directly into design reviews. It automates threat identification based on system components and clearly highlights missing mitigations.
Best suited for organizations using Microsoft development ecosystems (Azure, .NET) where native integration with existing workflows reduces adoption friction.
2. OWASP Threat Dragon
A lightweight, browser-based tool that supports collaborative modeling, basic STRIDE workflows, and diagramming through a simple UI. Its GitHub integration makes it easy to version and review threat models alongside code.
Recommended for teams practicing infrastructure-as-code methodologies who need threat models stored in version control systems rather than standalone databases.
3. IriusRisk
A commercial, automation-heavy platform used by enterprises. It generates threat libraries automatically, scores risk severity, provides built-in mitigation guidance, and syncs directly with Jira or Azure DevOps. Useful for organizations that need scaling, reporting, and consistency.
Particularly valuable for regulated industries requiring audit trails, compliance mapping, and automated risk scoring across multiple product teams.
4. ThreatModeler
A cloud-focused modeling tool that helps teams build reusable threat libraries, model complex architectures, and assess cloud configurations. It excels in large or rapidly evolving environments with many microservices and integrations.
Designed specifically for cloud-native architectures using containerization, serverless functions, and distributed service meshes where traditional network-boundary threat models prove insufficient.
5. OWASP PyTM
A code-centric modeling framework where threat models are written as Python scripts. This appeals to engineering teams that prefer version-controlled, testable, programmable definitions rather than drag-and-drop diagrams.
Ideal for DevSecOps teams who treat security artifacts as code – enabling automated threat model validation in CI/CD pipelines and programmatic updates when architecture changes.
Pentesting tools
1. Burp Suite (professional)
The most widely used toolkit for web application pentesting. It includes intercepting proxies, automated scanners, crawler engines, and rich manual exploitation features. Excellent for testing authentication flows, input validation, and complex application logic.
Industry standard for manual web application security testing, particularly for applications with complex business logic, multi-step workflows, and custom authentication mechanisms that automated scanners miss.
2. Metasploit Framework
A powerful exploitation platform with thousands of publicly available modules. It helps security teams simulate real attacker behavior, chain vulnerabilities, and validate how deeply an adversary could move within a system.
Essential for post-exploitation analysis and lateral movement testing – validating whether network segmentation, privilege controls, and detection systems function effectively once initial access is achieved.
3. Nmap
A foundational tool for network discovery and service fingerprinting. It identifies open ports, exposed services, and configuration weaknesses that often form the first step in real-world attack chains.
The reconnaissance standard for mapping attack surfaces before deeper testing, particularly critical for understanding external exposure, third-party integrations, and shadow IT that threat models may have overlooked.
4. OWASP ZAP (Zed Attack Proxy)
An open-source alternative to Burp that excels in automation. ZAP integrates well with CI/CD pipelines, making it a strong choice for recurring scans during development and release cycles.
Optimized for shift-left security practices where automated vulnerability scanning runs with every build – providing developers immediate feedback on common web vulnerabilities (XSS, SQL injection, CSRF) before code review.
5. Nessus
A comprehensive vulnerability scanner used to detect misconfigurations, missing patches, and known CVEs across servers, APIs, cloud workloads, and networks. Its depth and update frequency make it a reliable enterprise standard.
Primary tool for infrastructure vulnerability management, continuously monitoring production and staging environments for configuration drift, unpatched systems, and compliance violations that create exploitable attack vectors.
Building an integrated toolchain
Most mid-market and enterprise teams combine open-source tools with commercial platforms, rather than relying on a single product.
They integrate threat modeling outputs into pentest scope, automate scans through CI/CD, sync mitigation tasks with ticketing systems, and maintain a unified risk library across engineering and security.
This hybrid approach keeps security costs manageable while enabling consistent, repeatable workflows that scale across teams and releases, a practical model similar to how companies structure machine learning development pipelines with continuous training, validation, and deployment phases.
The most mature security programs establish bidirectional data flows between these tool categories. Threat modeling platforms export risk priorities that configure automated scanner rulesets, while pentesting tools feed discovered vulnerabilities back into threat model assumptions. This creates a closed-loop system where each practice continuously improves the accuracy of the other.
From compliance to continuous security
Many organizations still approach security through a "compliance checkbox" lens – run a pentest once a year, submit the report, and assume the system is safe.
This point-in-time assessment model creates a fundamental mismatch: the audit captures a single snapshot while the environment continuously changes through new features, expanded integrations, infrastructure evolution, and adaptive attacker techniques. A static checklist cannot protect a dynamic system.
A continuous security model operates as an integrated lifecycle discipline where threat modeling and pentesting reinforce each other across the entire product lifecycle.
Teams analyze potential risks during design, validate real attack paths after deployment, and update both models and controls whenever the system changes. This produces a living security posture – one that is actionable, resilient, and consistently audit-ready.
Compliance-driven vs. continuous security: Core operational differences
The compliance-only approach fails because it:
- Treats security as an event rather than a lifecycle discipline, creating long gaps where new vulnerabilities remain undetected
- Produces audit artifacts without validating ongoing control effectiveness, providing auditors with historical reports, not current assurance
- Incentivizes reactive patching over architectural improvements, encouraging quick fixes instead of systemic risk reduction
- Ignores system evolution, missing risks introduced through architecture changes, new dependencies, and shifting user behavior
Continuous security enables:
- Proactive risk identification – detecting design flaws through recurring threat modeling before code deployment
- Event-driven validation, triggering pentesting whenever systems or features change, not on arbitrary schedules
- Continuous compliance evidence, generating traceable improvement records that satisfy audits without dedicated preparation cycles
- Cost-optimized risk management, addressing vulnerabilities during design when remediation costs 10-100x less than post-deployment fixes
- Real-time risk visibility, maintaining an always-current exposure assessment rather than relying on aging annual snapshots
This operational shift transforms security from a compliance burden into a strategic capability – one that simultaneously satisfies regulatory requirements, resists active threats, and adapts to rapid product evolution without requiring teams to choose between speed and safety.
Conclusion
Threat modeling and penetration testing aren't competing methodologies but sequential phases in a mature security lifecycle.
Threat modeling predicts architectural risks during design; pentesting validates control effectiveness in production. Organizations that integrate both practices shift from reactive vulnerability management to proactive security engineering, reducing costs while improving resilience.
For engineering leaders building security programs under budget constraints, this integrated approach delivers three strategic advantages:
- earlier risk detection (preventing expensive post-deployment fixes);
- validated security posture (audit-ready evidence that controls actually work);
- and continuous improvement (security capabilities that scale with product complexity).
If your organization needs support structuring this workflow – from initial threat model development through targeted penetration testing and ongoing security operations – Binariks provides end-to-end security engineering services that align technical controls with business risk.
Contact us to explore our security practice to build a program grounded in both design analysis and real-world validation.
Share

