As the realm of IoMT devices continues to expand, IoMT security remains an important concern within today's interconnected healthcare ecosystem.
The fusion of medical technology with the internet has paved the way for revolutionary patient care and treatment advancements. However, this convergence also brings forth many security challenges that must be addressed comprehensively.
The interconnected nature of IoMT devices exposes them to potential vulnerabilities that could compromise patient privacy, data integrity, and even patient safety. Threats such as unauthorized access, data breaches, and malicious attacks loom large, necessitating a proactive approach to safeguarding these devices and the sensitive data they handle.
In this guide, we will explore IoMT cybersecurity to reveal the risks and uncover the best strategies and practices to protect this evolving ecosystem against potential threats.
Exploring IoMT (Internet of Medical Things)
At its core, the IoMT refers to the network of medical devices and applications that are interconnected through the internet, allowing them to collect, exchange, and analyze data in real-time.
This interconnected ecosystem encompasses many devices, including wearable health trackers, smart medical implants, remote patient monitoring systems, and diagnostic equipment. The IoMT promises to transform healthcare by facilitating proactive patient care and enhancing medical decision-making through data-driven approaches.
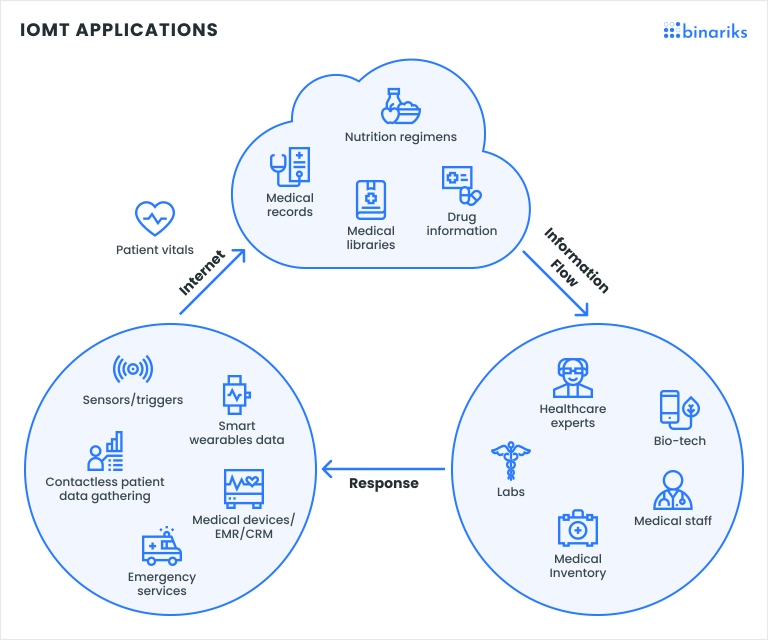
As the IoMT advances, it introduces a paradigm shift in how healthcare is delivered and experienced. Real-time data sharing enables healthcare providers to monitor patients remotely, personalize treatment plans, and make informed decisions swiftly.
Patients themselves gain more control over their health, accessing personalized insights and tracking their progress conveniently.
While the benefits are evident, the IoMT also presents challenges, primarily centered around security and privacy. As devices become more interconnected, the potential for unauthorized access and data breaches increases. Healthcare needs a delicate balance between harnessing the potential of the IoMT and addressing its associated challenges.
In one of our previous articles, you can learn more about the general impact of the Internet of Medical Things (IoMT) on healthcare delivery.
IoMT devices security risks & challenges
According to KPMG Healthcare and Cybersecurity research, the most important cyber security concerns for healthcare providers and payers are coming from external sources (Source ).

Risks
Medical iot security is fraught with potential risks that demand vigilant safeguards to protect patient safety and data integrity.
- Patient Safety: Compromised security for IoT devices could lead to misdiagnosis, incorrect treatment administration, and even life-threatening consequences for patients.
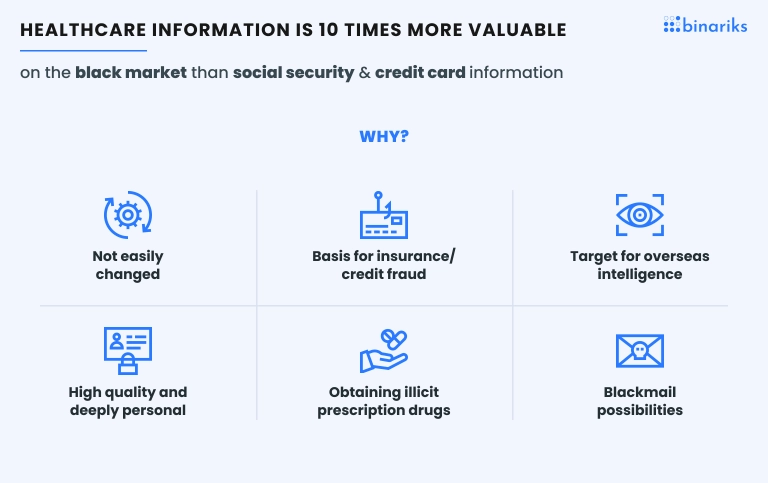
- Data Breaches: The exposure of sensitive patient information due to breaches could result in identity theft, fraud, and violation of patient privacy.
- Ransomware Attacks: Ransomware incidents could disrupt healthcare operations, locking providers out of crucial systems until ransoms are paid, potentially impacting patient care.
- Malware Attacks: Malicious software can infiltrate and compromise the functionality of IoMT devices, impacting their accuracy and effectiveness.
- Device Hijacking: Unauthorized access to control medical devices could lead to unauthorized manipulation, posing grave risks to patient well-being.
Challenges
The security challenges within the IoMT landscape are multifaceted, demanding comprehensive strategies to mitigate potential problems.
- Vulnerabilities: IoMT devices may have security vulnerabilities that hackers can exploit, gaining unauthorized access to sensitive data or disrupting device functionality.
- Data Privacy: The seamless flow of patient data across interconnected devices raises concerns about maintaining patient privacy and protecting against unauthorized access.
- Interoperability: Ensuring seamless communication and compatibility among diverse IoMT devices can be challenging, potentially leading to security gaps.
- Regulatory Compliance Problems: Navigating evolving regulatory standards poses challenges to ensuring IoMT systems adhere to privacy and security requirements.
Addressing IoMT security risks and challenges requires a holistic approach that encompasses technological innovation, policy development, and ongoing vigilance to safeguard patient well-being and the integrity of medical data.
IoMT security best practices: 5 ways to protect
With this level of connectivity comes a heightened risk of security and data breaches. In this block, we'll explore five security best practices IoT development services and medical companies use to safeguard IoMT infrastructure and sensitive information.
1. Asset inventory
Before you can secure your IoMT environment effectively, you need to know what you're protecting. Start by creating a comprehensive inventory of all your IoMT devices. This includes not only medical devices like infusion pumps and pacemakers but also network infrastructure components.
Regularly update this inventory to ensure you know all the devices connected to your network. This information is crucial for monitoring and managing security risks effectively.
2. Strong password policy
Implementing a robust password policy is a fundamental step in IoT security for healthcare.
Ensure that all devices and systems in your IoMT network use strong, unique passwords. Avoid default usernames and passwords, as these are often targeted by attackers. Enforce regular password changes and educate your staff on creating strong passwords. Use password management tools to facilitate secure password management and reduce the risk of credential-based attacks.
3. Multi-factor authentication
Multi-factor authentication (MFA) is an essential security measure that adds an extra layer of protection to your IoMT devices and systems. It requires users to provide two or more verification factors, such as something they know (password), something they have (smart card or mobile app), or something they are (fingerprint or retina scan).
By implementing MFA, you can significantly reduce the risk of unauthorized access even if a password is compromised.
4. Network segmentation
Network segmentation involves dividing your IoMT network into smaller, isolated segments. Each segment should have its own security measures and access controls.
By implementing network segmentation, you can contain security breaches, prevent lateral movement by attackers, and limit the impact of a compromise on a specific segment. This approach enhances overall network security and protects critical healthcare systems and data.
5. Security patch updates
Regularly updating the software and firmware of IoMT devices and network infrastructure is crucial for addressing vulnerabilities and security flaws. Manufacturers often release patches and updates to fix known security issues.
Establish a robust patch management process to ensure timely deployment of these updates. Keep track of security advisories related to your IoMT devices and apply patches promptly to mitigate potential risks.
Let’s team up for IoT acceleration
Some medical IoT (IoMT) cyber security vendors
Many dedicated cybersecurity vendors have emerged to address the unique challenges of IoMT devices security. These vendors specialize in providing tailored solutions to enhance the security for IoMT, mitigating risks, and fortifying defenses against potential threats.
As the industry continues to evolve, the role of these vendors becomes increasingly important in ensuring the safety and integrity of medical data and device functionality. Here are some well-known companies in this field.
Cinerio
Established in 2017 by a diverse team of cybersecurity, medical device, and healthcare IT experts, Cynerio operates from New York City, collaborating with global Healthcare Delivery Organizations (HDOs). Cynerio offers a distinctive medical-centric cybersecurity solution, equipping clinical ecosystems with the security needed for uninterrupted patient care and operational assurance.
Cynerio presents a comprehensive healthcare IoT cybersecurity approach prioritizing patient care and privacy. Their agentless solution analyzes device communication and behavior to offer ongoing risk assessments, enabling swift and nonintrusive remediation aligned with healthcare business goals.
This empowers HDOs to regain control over clinical assets and attain immediate security goals while planning for long-term security objectives. With Cynerio's expertise, how to secure IoMT becomes a focused endeavor, allowing healthcare organizations to navigate the complexities of interconnected medical devices with confidence.
Medigate
Medigate presents a comprehensive IoT cybersecurity platform with capabilities that redefine clinical visibility. Collaborating globally with health systems, Medigate partners to monetize risk reduction practices and enhance clinical outcomes.
Powered by deep packet inspection (DPI), Medigate's deterministic approach resolves intricate medical device protocols. This yields superior data quality, enabling strategic system integrations and new use-cases that elevate risk reduction to a revenue-generating practice.
Sternum
Founded in 2018 in Tel Aviv, Sternum redefines medical IoT security by offering real-time, embedded protection for IoT devices. Backed by experienced R&D and business leaders, Sternum sets a new standard for cybersecurity in medical IoT devices, compliant with FDA guidelines and equipped with unique technology that safeguards patients' lives.
Sternum's Embedded Integrity Verification (EIV) detects and prevents real-time cyber attacks, functioning as an on-device firewall that ensures protection throughout a device's lifecycle. This solution combats zero-day attacks in real time and offers unparalleled monitoring beyond network confines, addressing the sphere of IoMT security challenges.
Binariks for your IoMT cybersecurity
Binariks makes no compromise on cybersecurity. Our expertise extends to both integrating ready-made software and building сustom healthcare solutions in compliance with all the required industry standards.
Besides, we offer ongoing support and maintenance to ensure the developed IoMT solution (or any other software or application) remains current with the latest security updates and compliance demands. With Binariks at your side, you're getting a reliable tech partner committed to empowering your healthcare organization to thrive securely in the digital age and navigate challenges with confidence.
Contact us today to learn how our expertise can help you build a secure, high-performing, and scalable IoMT solution.
Conclusion
The importance of saving patient well-being, data integrity, and operational continuity has led to the emergence of robust IoMT risk monitoring solutions and sophisticated IoMT security software. As organizations embrace the potential of interconnected medical devices, they must remain steadfast in their commitment to effective cybersecurity practices.
By adopting a holistic approach that combines technological advancements, vigilant risk assessment, and a proactive stance on security, healthcare organizations can confidently navigate the complexities of the IoMT. As the field continues to evolve, staying informed about the latest developments and best practices will remain paramount in ensuring patient safety, data integrity, and the seamless operation of medical ecosystems in the digital age.
FAQ
Share

